CRYPTOGRAPHY: A SHORT
TUTORIAL
Air Force Captain Ir. Arwin “Daemon”
Sumari, FSI, FSME, VDBM, SA
(Head of
Simulator Operation, Training Facility, 3rd Fighter Wing, Iswahjudi
AFB)
Information security
probably is the most important thing in communication community especially
military. Talking about
information security is equal to talking about a technology involving in this
business that is cryptography.
A definition taken from “Handbook
of Applied Cryptography” published by CRC Press, Inc. writes that Cryptography is the study of
mathematical techniques related to aspects of information security such as
confidentiality, data integrity, entity authentication and data origin
authentication. In the
military world, the kind of cryptography used is strong cryptography. The strong cryptography is used to
protect information of real value against organized criminals, multinational
corporations and major governments.
In broad meaning, cryptography is about the prevention and detection of
cheating and other malicious activities.
Cryptographic
Goals
There are four goals
that must be achieved both in theory and practice that is (1) privacy or confidentiality; (2) data integrity; (3) authentication; and (4) non-repudiation.
Q
Confidentiality or secrecy is a service used to keep the
content of information from all but those authorized to have it. There are numerous approaches to
providing confidentiality, ranging from physical protection to mathematical
algorithms which render data unintelligible that can be implemented in form of
computer software.
Q
Data
integrity is a service which
addresses the unauthorized alteration of data. To assure data integrity, one must have
the ability to detect data manipulation by unauthorized parties or
entities. Data manipulation
includes such things as insertion, deletion and
substitution.
Q
Authentication is a service related to
identification. This function
applies to both parties and information itself. Two parties entering into a
communication should identify each other. Information delivered over a
channel should be authenticated as to origin, date of origin, data content, time
sent, etc. For these reasons
this aspect of cryptography is usually subdivide into two major classes: entity
authentication and data authentication.
Data origin authentication itself implicitly provides data
integrity.
Q
Non-repudiation is a service which
prevents an entity from denying previous commitments or actions. When disputes arise due to an
entity denying that certain actions were taken, a means to resolve the situation
is necessary.
A simple model of a two-party communication using encryption is provided by figure 1.
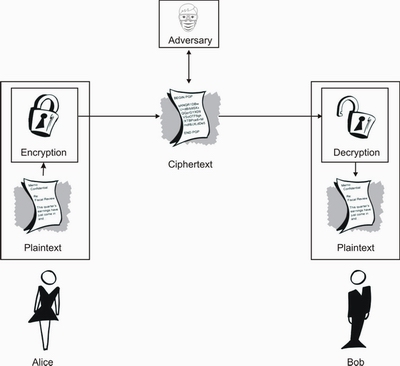
Figure 1. Schematic of a two-party
communication using encryption.
From the figure 1 we
have some new terms and their definition are:
Ü
An entity or party is someone or something which
sends, receives, or manipulates information. Alice and Bob are entities. An entity may be a person, a computer
terminal, etc.
Ü
A sender is an entity in a two-party communication
which is the legitimate transmitter of information. In figure 1, the sender is
Ü
A receiver is an entity in a two-party
communication which is the intended recipient of information. In figure 1, the receiver is
Bob.
Ü
An adversary is an entity in a two-party
communication which is neither the sender nor the receiver, and which tries to
defeat the information security service being provided between the sender and
receiver. The other names for
adversary are opponent, enemy, attacker,
tapper, eavesdropper, intruder, and
interloper. An adversary will
often attempt to play the role of either the legitimate sender or the legitimate
receiver. There are two types of adversary as followed :
Æ
Passive
adversary that is only capable of
reading information from an unsecured communication
channel.
Æ
Active
adversary that is able to
transmit, alter, or delete information on an unsecured communication
channel.
Ü
A channel is a means of conveying
information from one entity to another. A channel can be subdivided into
three definitions, that is :
Æ
Physically secure
channel
or secure channel is one which is not
physically accessible to the adversary.
Æ
Unsecured
channel
is one from which parties other than those for which the information is intended
can reorder, delete, insert, or read.
Æ
Secured
channel
is one from which an adversary does not have the ability to reorder, delete,
insert, or read.
Cryptographic
Techniques
The techniques typically
are divided into two generic types: symmetric-key cipher and asymmetric-key or public-key cipher. Cipher is a method for encrypting and
decrypting information. Plaintext is synonym for information and
ciphertext is encrypted
information.
G
Symmetric-Key
Cipher

Figure 2. Schematic of Symmetric-Key Cipher
Technique.
Symmetric-key cipher
uses the same secret-key
for encryption and decryption. Secret-key is a key that must be kept secret
between the sender and recipient of information. In general, symmetric-key cipher
can use short keys (usually from 64 to 128 bits) and is therefore much faster to
execute than asymmetric ones, but they need a secure channel between the sender
and the recipient of a message since they both have to know the secret key.
Symmetric-key cipher can be further divided into stream ciphers which can
encrypt a single bit of plaintext
at a time and block ciphers which take a number of bits (typically 64 in
modern ciphers) and encrypt them as a single unit. Well-known symmetric ciphers
include the data encryption standard (DES) and the international data
encryption algorithm (IDEA).
G
Asymmetric (Public-Key)
Cipher
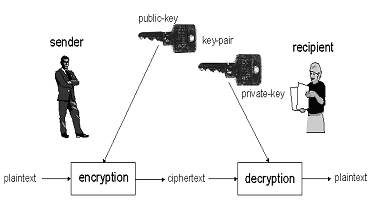
Figure 3. Schematic of Asymmetric-Key Cipher
Technique.
Asymmetric cipher
use key-pairs consisting of a public-key
made available for public and a private-key
only known to one individual - the owner of the public/private key-pair. Theses
ciphers assume the private key to be not derivable from the public key
and vice-versa. Some algorithms make this problem equivalent to factoring a
large number being composed of two large prime factors or to computing the
discrete logarithm modulo a large number. Asymmetric-key cipher needs longer
keys (usually from 512 to 1024 bits) and is therefore slower than symmetric-key
cipher, but they solve the problem of a secure channel between the sender and
the recipient of a message. Probably the best known asymmetric-key cipher is
called RSA
(Rivest-Shamir-Adelman).
Classes of
Attacks
Over the years, many
different types of attacks on cryptographic techniques have been
identified. There are two
kinds of attacks: passive attack and
active attack.
F
A passive attack is one where the
adversary only monitors the communication channel and only threatens
confidentiality of data.
F
An active attack is one where the adversary
attempts to delete, add, or in some other way alter the transmission on the
channel. An active attacker
threatens data integrity and authentication as well as
confidentiality.
A passive attack can be
further subdivided into more specialized attacks for deducing plaintext from
chipertext as listed followed:
þ
Ciphertext-only
attack. The adversary tries to deduce the
decryption key or plaintext by only observing ciphertext.
þ
Known-plaintext
attack. The adversary has a quantity of
plaintext and corresponding ciphertext.
þ
Chosen-plaintext
attack. The adversary chooses plaintext
and is then given corresponding ciphertext. Subsequently, the adversary uses
any information deduced in order to recover plaintext corresponding to
previously unseen ciphertext.
þ
Adaptive
chosen-plaintext attack. It is a chosen-plaintext attack wherein
the choice of plaintext may depend on the ciphertext received from previous
request.
þ
Chosen-ciphertext
attack. The adversary selects the ciphertext and
is then given the corresponding plaintext.
The objective is to be able to deduce the plaintext from (different)
ciphertext.
þ
Adaptive
chosen-ciphertext attack. It is a chosen-ciphertext attack where
the choice of ciphertext may depend on the plaintext received from previous
requests.